[ad_1] Feb 16, 2024NewsroomEndpoint Security / Cryptocurrency Multiple companies operating in the cryptocurrency sector are the target of an ongoing malware campaign that involves a newly discovered Apple macOS backdoor codenamed RustDoor. RustDoor was first documented by Bitdefender last week, describing it as a Rust-based malware capable of harvesting and uploading files, as well as…
Month: February 2024
Akira Ransomware Exploiting Cisco ASA/FTD Vulnerability
[ad_1] Feb 16, 2024NewsroomRansomware / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a now-patched security flaw impacting Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) software to its Known Exploited Vulnerabilities (KEV) catalog, following reports that it’s being likely exploited in Akira ransomware attacks. The vulnerability in question…
Google Open Sources Magika: AI-Powered File Identification Tool
[ad_1] Feb 17, 2024NewsroomArtificial Intelligence / Data Protection Google has announced that it’s open-sourcing Magika, an artificial intelligence (AI)-powered tool to identify file types, to help defenders accurately detect binary and textual file types. “Magika outperforms conventional file identification methods providing an overall 30% accuracy boost and up to 95% higher precision on traditionally hard…
How Businesses Can Safeguard Their Communication Channels Against Hackers
[ad_1] Efficient communication is a cornerstone of business success. Internally, making sure your team communicates seamlessly helps you avoid friction losses, misunderstandings, delays, and overlaps. Externally, frustration-free customer communication is directly correlated to a positive customer experience and higher satisfaction. However, business communication channels are also a major target for cybercriminals. In recent years, especially…
FBI’s Most-Wanted Zeus and IcedID Malware Mastermind Pleads Guilty
[ad_1] Feb 18, 2024NewsroomMalware / Cybercrime A Ukrainian national has pleaded guilty in the U.S. to his role in two different malware schemes, Zeus and IcedID, between May 2009 and February 2021. Vyacheslav Igorevich Penchukov (aka Vyacheslav Igoravich Andreev, father, and tank), 37, was arrested by Swiss authorities in October 2022 and extradited to the…
Iranian Hackers Target Middle East Policy Experts with New BASICSTAR Backdoor
[ad_1] Feb 19, 2024NewsroomMalware / Cyber Espionage The Iranian-origin threat actor known as Charming Kitten has been linked to a new set of attacks aimed at Middle East policy experts with a new backdoor called BASICSTAR by creating a fake webinar portal. Charming Kitten, also called APT35, CharmingCypress, Mint Sandstorm, TA453, and Yellow Garuda, has…
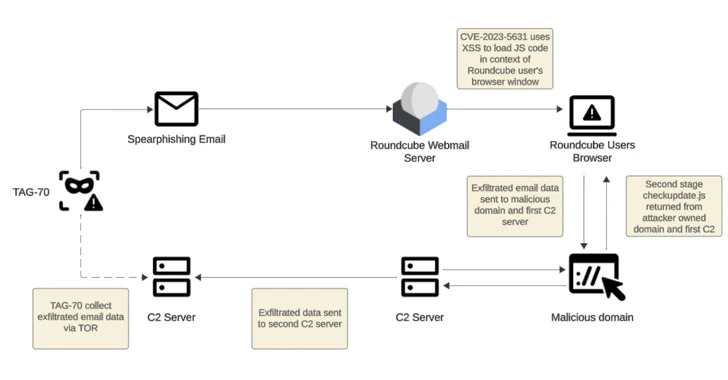
Russian-Linked Hackers Target 80+ Organizations via Roundcube Flaws
[ad_1] Feb 19, 2024NewsroomCyber Espionage / Vulnerability Threat actors operating with interests aligned to Belarus and Russia have been linked to a new cyber espionage campaign that likely exploited cross-site scripting (XSS) vulnerabilities in Roundcube webmail servers to target over 80 organizations. These entities are primarily located in Georgia, Poland, and Ukraine, according to Recorded…
Anatsa Android Trojan Bypasses Google Play Security, Expands Reach to New Countries
[ad_1] The Android banking trojan known as Anatsa has expanded its focus to include Slovakia, Slovenia, and Czechia as part of a new campaign observed in November 2023. “Some of the droppers in the campaign successfully exploited the accessibility service, despite Google Play’s enhanced detection and protection mechanisms,” ThreatFabric said in a report shared with…
Dormant PyPI Package Compromised to Spread Nova Sentinel Malware
[ad_1] Feb 23, 2024NewsroomSupply Chain Attack / Malware A dormant package available on the Python Package Index (PyPI) repository was updated nearly after two years to propagate an information stealer malware called Nova Sentinel. The package, named django-log-tracker, was first published to PyPI in April 2022, according to software supply chain security firm Phylum, which…
How to Achieve the Best Risk-Based Alerting (Bye-Bye SIEM)
[ad_1] Did you know that Network Detection and Response (NDR) has become the most effective technology to detect cyber threats? In contrast to SIEM, NDR offers adaptive cybersecurity with reduced false alerts and efficient threat response. Are you aware of Network Detection and Response (NDR) and how it’s become the most effective technology to detect…