[ad_1] Apr 30, 2024NewsroomDocker Hub / Supply Chain Attack Cybersecurity researchers have discovered multiple campaigns targeting Docker Hub by planting millions of malicious “imageless” containers over the past five years, once again underscoring how open-source registries could pave the way for supply chain attacks. “Over four million of the repositories in Docker Hub are imageless…
Month: April 2024
U.S. Government Releases New AI Security Guidelines for Critical Infrastructure
[ad_1] Apr 30, 2024NewsroomMachine Learning / National Security The U.S. government has unveiled new security guidelines aimed at bolstering critical infrastructure against artificial intelligence (AI)-related threats. “These guidelines are informed by the whole-of-government effort to assess AI risks across all sixteen critical infrastructure sectors, and address threats both to and from, and involving AI systems,”…
China-Linked ‘Muddling Meerkat’ Hijacks DNS to Map Internet on Global Scale
[ad_1] A previously undocumented cyber threat dubbed Muddling Meerkat has been observed undertaking sophisticated domain name system (DNS) activities in a likely effort to evade security measures and conduct reconnaissance of networks across the world since October 2019. Cloud security firm Infoblox described the threat actor as likely affiliated with the People’s Republic of China…
Google Prevented 2.28 Million Malicious Apps from Reaching Play Store in 2023
[ad_1] Apr 29, 2024NewsroomMobile Security / Hacking Google on Monday revealed that almost 200,000 app submissions to its Play Store for Android were either rejected or remediated to address issues with access to sensitive data such as location or SMS messages over the past year. The tech giant also said it blocked 333,000 bad accounts…
Okta Warns of Unprecedented Surge in Proxy-Driven Credential Stuffing Attacks
[ad_1] Apr 28, 2024NewsroomCredential Stuffing / Data Breach Identity and access management (IAM) services provider Okta has warned of a spike in the “frequency and scale” of credential stuffing attacks aimed at online services. These unprecedented attacks, observed over the last month, are said to be facilitated by “the broad availability of residential proxy services,…
Palo Alto Networks Outlines Remediation for Critical PAN-OS Flaw Under Attack
[ad_1] Apr 26, 2024NewsroomNetwork Security / Zero Day Palo Alto Networks has shared remediation guidance for a recently disclosed critical security flaw impacting PAN-OS that has come under active exploitation. The vulnerability, tracked as CVE-2024-3400 (CVSS score: 10.0), could be weaponized to obtain unauthenticated remote shell command execution on susceptible devices. It has been addressed…
Bogus npm Packages Used to Trick Software Developers into Installing Malware
[ad_1] Apr 27, 2024NewsroomMalware / Software Security An ongoing social engineering campaign is targeting software developers with bogus npm packages under the guise of a job interview to trick them into downloading a Python backdoor. Cybersecurity firm Securonix is tracking the activity under the name DEV#POPPER, linking it to North Korean threat actors. “During these…
Ukraine Targeted in Cyberattack Exploiting 7-Year-Old Microsoft Office Flaw
[ad_1] Apr 27, 2024NewsroomCyber Attack / Malware Cybersecurity researchers have discovered a targeted operation against Ukraine that has been found leveraging a nearly seven-year-old flaw in Microsoft Office to deliver Cobalt Strike on compromised systems. The attack chain, which took place at the end of 2023 according to Deep Instinct, employs a PowerPoint slideshow file…
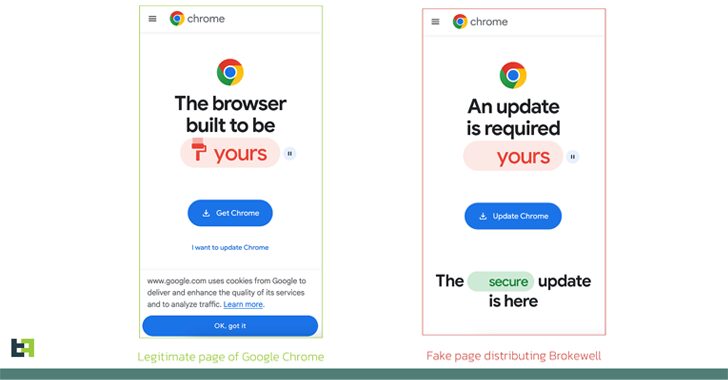
New ‘Brokewell’ Android Malware Spread Through Fake Browser Updates
[ad_1] Apr 26, 2024NewsroomMobile Security / Cybercrime Fake browser updates are being used to push a previously undocumented Android malware called Brokewell. “Brokewell is a typical modern banking malware equipped with both data-stealing and remote-control capabilities built into the malware,” Dutch security firm ThreatFabric said in an analysis published Thursday. The malware is said to…
Severe Flaws Disclosed in Brocade SANnav SAN Management Software
[ad_1] Apr 26, 2024NewsroomSupply Chain Attack / Software Security Several security vulnerabilities disclosed in Brocade SANnav storage area network (SAN) management application could be exploited to compromise susceptible appliances. The 18 flaws impact all versions up to and including 2.3.0, according to independent security researcher Pierre Barre, who discovered and reported them. The issues range…