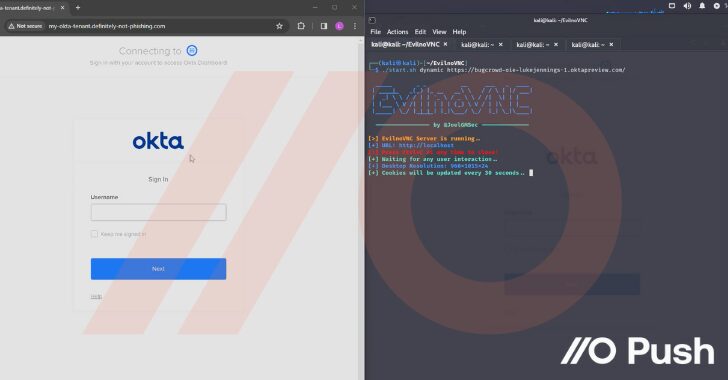
[ad_1] Attackers are increasingly making use of “networkless” attack techniques targeting cloud apps and identities. Here’s how attackers can (and are) compromising organizations – without ever needing to touch the endpoint or conventional networked systems and services. Before getting into the details of the attack techniques being used, let’s discuss why these attacks are becoming…
Month: April 2024
FIN7 Cybercrime Group Targeting U.S. Auto Industry with Carbanak Backdoor
[ad_1] Apr 18, 2024NewsroomCyber Attack / Malware The infamous cybercrime syndicate known as FIN7 has been linked to a spear-phishing campaign targeting the U.S. automotive industry to deliver a known backdoor called Carbanak (aka Anunak). “FIN7 identified employees at the company who worked in the IT department and had higher levels of administrative rights,” the…
OfflRouter Malware Evades Detection in Ukraine for Almost a Decade
[ad_1] Apr 18, 2024NewsroomIncident Response / Cyber Espionage Select Ukrainian government networks have remained infected with a malware called OfflRouter since 2015. Cisco Talos said its findings are based on an analysis of over 100 confidential documents that were infected with the VBA macro virus and uploaded to the VirusTotal malware scanning platform. “The documents…
Recover from Ransomware in 5 Minutes—We will Teach You How!
[ad_1] Super Low RPO with Continuous Data Protection: Dial Back to Just Seconds Before an Attack Zerto, a Hewlett Packard Enterprise company, can help you detect and recover from ransomware in near real-time. This solution leverages continuous data protection (CDP) to ensure all workloads have the lowest recovery point objective (RPO) possible. The most valuable…
Critical Atlassian Flaw Exploited to Deploy Linux Variant of Cerber Ransomware
[ad_1] Apr 17, 2024NewsroomEncryption / Vulnerability Threat actors are exploiting unpatched Atlassian servers to deploy a Linux variant of Cerber (aka C3RB3R) ransomware. The attacks leverage CVE-2023-22518 (CVSS score: 9.1), a critical security vulnerability impacting the Atlassian Confluence Data Center and Server that allows an unauthenticated attacker to reset Confluence and create an administrator account….
Russian APT Deploys New ‘Kapeka’ Backdoor in Eastern European Attacks
[ad_1] Apr 17, 2024NewsroomRansomware / Cyber Espionage A previously undocumented “flexible” backdoor called Kapeka has been “sporadically” observed in cyber attacks targeting Eastern Europe, including Estonia and Ukraine, since at least mid-2022. The findings come from Finnish cybersecurity firm WithSecure, which attributed the malware to the Russia-linked advanced persistent threat (APT) group tracked as Sandworm…
A New Headache for SaaS Security Teams
[ad_1] The introduction of Open AI’s ChatGPT was a defining moment for the software industry, touching off a GenAI race with its November 2022 release. SaaS vendors are now rushing to upgrade tools with enhanced productivity capabilities that are driven by generative AI. Among a wide range of uses, GenAI tools make it easier for…
TA558 Hackers Weaponize Images for Wide-Scale Malware Attacks
[ad_1] Apr 16, 2024NewsroomThreat Intelligence / Endpoint Security The threat actor tracked as TA558 has been observed leveraging steganography as an obfuscation technique to deliver a wide range of malware such as Agent Tesla, FormBook, Remcos RAT, LokiBot, GuLoader, Snake Keylogger, and XWorm, among others. “The group made extensive use of steganography by sending VBSs,…
OpenJS Foundation Targeted in Potential JavaScript Project Takeover Attempt
[ad_1] Apr 16, 2024NewsroomSupply Chain / Software Security Security researchers have uncovered a “credible” takeover attempt targeting the OpenJS Foundation in a manner that evokes similarities to the recently uncovered incident aimed at the open-source XZ Utils project. “The OpenJS Foundation Cross Project Council received a suspicious series of emails with similar messages, bearing different…
Widely-Used PuTTY SSH Client Found Vulnerable to Key Recovery Attack
[ad_1] Apr 16, 2024NewsroomEncryption / Network Security The maintainers of the PuTTY Secure Shell (SSH) and Telnet client are alerting users of a critical vulnerability impacting versions from 0.68 through 0.80 that could be exploited to achieve full recovery of NIST P-521 (ecdsa-sha2-nistp521) private keys. The flaw has been assigned the CVE identifier CVE-2024-31497, with…