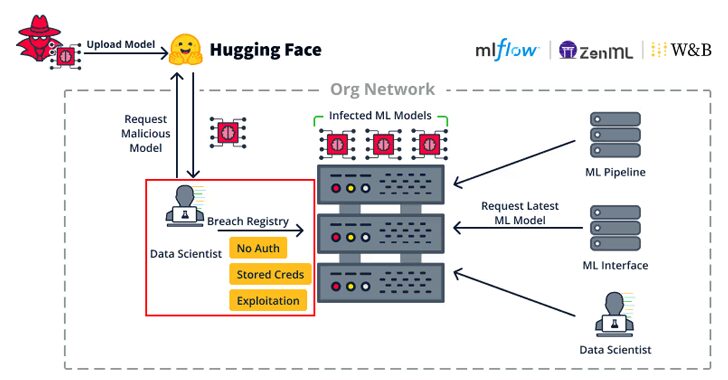
[ad_1] Dec 06, 2024Ravie LakshmananArtificial Intelligence / Vulnerability Cybersecurity researchers have disclosed multiple security flaws impacting open-source machine learning (ML) tools and frameworks such as MLflow, H2O, PyTorch, and MLeap that could pave the way for code execution. The vulnerabilities, discovered by JFrog, are part of a broader collection of 22 security shortcomings the supply…
Month: December 2024
FSB Uses Trojan App to Monitor Russian Programmer Accused of Supporting Ukraine
[ad_1] Dec 06, 2024Ravie LakshmananSpyware / Mobile Security A Russian programmer accused of donating money to Ukraine had his Android device secretly implanted with spyware by the Federal Security Service (FSB) after he was detained earlier this year. The findings come as part of a collaborative investigation by First Department and the University of Toronto’s…
Hackers Leveraging Cloudflare Tunnels, DNS Fast-Flux to Hide GammaDrop Malware
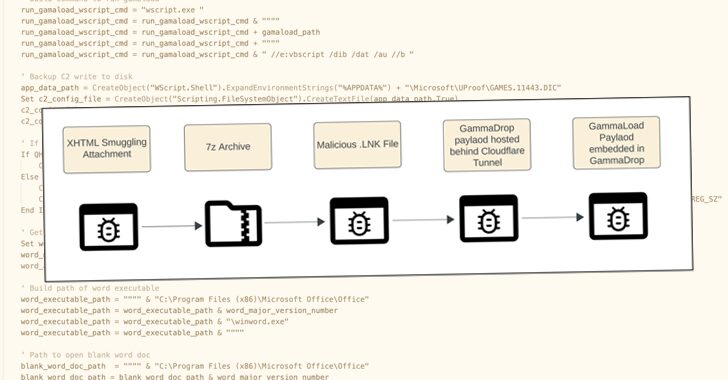
[ad_1] Dec 06, 2024The Hacker NewsMalware / Threat Intelligence The threat actor known as Gamaredon has been observed leveraging Cloudflare Tunnels as a tactic to conceal its staging infrastructure hosting a malware called GammaDrop. The activity is part of an ongoing spear-phishing campaign targeting Ukrainian entities since at least early 2024 that’s designed to drop…
Critical Mitel MiCollab Flaw Exposes Systems to Unauthorized File and Admin Access
[ad_1] Dec 05, 2024Ravie LakshmananVulnerability / IoT Security Cybersecurity researchers have released a proof-of-concept (PoC) exploit that strings together a now-patched critical security flaw impacting Mitel MiCollab with an arbitrary file read zero-day, granting an attacker the ability to access files from susceptible instances. The critical vulnerability in question is CVE-2024-41713 (CVSS score: 9.8), which…
This $3,000 Android Trojan Targeting Banks and Cryptocurrency Exchanges
[ad_1] Dec 05, 2024Ravie LakshmananCryptocurrency / Mobile Security As many as 77 banking institutions, cryptocurrency exchanges, and national organizations have become the target of a newly discovered Android remote access trojan (RAT) called DroidBot. “DroidBot is a modern RAT that combines hidden VNC and overlay attack techniques with spyware-like capabilities, such as keylogging and user…
ANEL and NOOPDOOR Backdoors Weaponized in New MirrorFace Campaign Against Japan
[ad_1] Dec 05, 2024Ravie LakshmananCyber Espionage / Malware The China-linked threat actor known as MirrorFace has been attributed to a new spear-phishing campaign mainly targeting individuals and organizations in Japan since June 2024. The aim of the campaign is to deliver backdoors known as NOOPDOOR (aka HiddenFace) and ANEL (aka UPPERCUT), Trend Micro said in…
Russia-Linked Turla Exploits Pakistani Hackers’ Servers to Target Afghan and Indian Entities
[ad_1] The Russia-linked advanced persistent threat (APT) group known as Turla has been linked to a previously undocumented campaign that involved infiltrating the command-and-control (C2) servers of a Pakistan-based hacking group named Storm-0156 to conduct its own operations since 2022. The activity, first observed in December 2022, is the latest instance of the nation-state adversary…
Europol Dismantles Criminal Messaging Service MATRIX in Major Global Takedown
[ad_1] Europol on Tuesday announced the takedown of an invite-only encrypted messaging service called MATRIX that’s created by criminals for criminal purposes. The joint operation, conducted by French and Dutch authorities under the moniker Passionflower, comes in the aftermath of an investigation that was launched in 2021 after the messaging service was discovered on the…
Joint Advisory Warns of PRC-Backed Cyber Espionage Targeting Telecom Networks
[ad_1] Dec 04, 2024Ravie Lakshmanan A joint advisory issued by Australia, Canada, New Zealand, and the U.S. has warned of a broad cyber espionage campaign undertaken by People’s Republic of China (PRC)-affiliated threat actors targeting telecommunications providers. “Identified exploitations or compromises associated with these threat actors’ activity align with existing weaknesses associated with victim infrastructure;…
NachoVPN Tool Exploits Flaws in Popular VPN Clients for System Compromise
[ad_1] Dec 03, 2024Ravie LakshmananEndpoint Security / Vulnerability Cybersecurity researchers have disclosed a set of flaws impacting Palo Alto Networks and SonicWall virtual private network (VPN) clients that could be potentially exploited to gain remote code execution on Windows and macOS systems. “By targeting the implicit trust VPN clients place in servers, attackers can manipulate…