[ad_1] Dec 11, 2024Ravie LakshmananRansomware / Malware Cybersecurity researchers have discovered a new version of the ZLoader malware that employs a Domain Name System (DNS) tunnel for command-and-control (C2) communications, indicating that the threat actors are continuing to refine the tool after resurfacing a year ago. “Zloader 2.9.4.0 adds notable improvements including a custom DNS…
Month: December 2024
Microsoft MFA AuthQuake Flaw Enabled Unlimited Brute-Force Attempts Without Alerts
[ad_1] Dec 11, 2024Ravie LakshmananVulnerability / Authentication Cybersecurity researchers have flagged a “critical” security vulnerability in Microsoft’s multi-factor authentication (MFA) implementation that allows an attacker to trivially sidestep the protection and gain unauthorized access to a victim’s account. “The bypass was simple: it took around an hour to execute, required no user interaction and did…
WordPress Hunk Companion Plugin Flaw Exploited to Silently Install Vulnerable Plugins
[ad_1] Dec 12, 2024Ravie LakshmananWebsite Security / Vulnerability Malicious actors are exploiting a critical vulnerability in the Hunk Companion plugin for WordPress to install other vulnerable plugins that could open the door to a variety of attacks. The flaw, tracked as CVE-2024-11972 (CVSS score: 9.8), affects all versions of the plugin prior to 1.9.0. The…
SaaS Budget Planning Guide for IT Professionals
[ad_1] SaaS services are one of the biggest drivers of OpEx (operating expenses) for modern businesses. With Gartner projecting $247.2 billion in global SaaS spending this year, it’s no wonder SaaS budgets are a big deal in the world of finance and IT. Efficient SaaS utilization can significantly affect both the bottom line and employee…
Researchers Uncover Symlink Exploit Allowing TCC Bypass in iOS and macOS
[ad_1] Dec 12, 2024Ravie LakshmananVulnerability / Device Security Details have emerged about a now-patched security vulnerability in Apple’s iOS and macOS that, if successfully exploited, could sidestep the Transparency, Consent, and Control (TCC) framework and result in unauthorized access to sensitive information. The flaw, tracked as CVE-2024-44131 (CVSS score: 5.3), resides in the FileProvider component,…
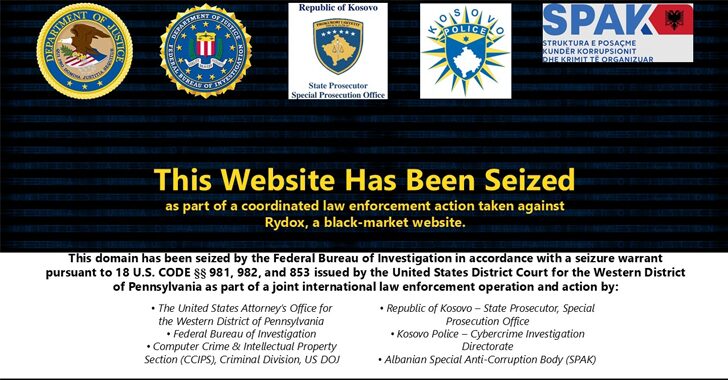
FBI Busts Rydox Marketplace with 7,600 PII Sales, Cryptocurrency Worth $225K Seized
[ad_1] The U.S. Department of Justice (DoJ) on Thursday announced the shutdown of an illicit marketplace called Rydox (“rydox[.]ru” and “rydox[.]cc”) for selling stolen personal information, access devices, and other tools for conducting cybercrime and fraud. In tandem, three Kosovo nationals and administrators of the service, Ardit Kutleshi, Jetmir Kutleshi, and Shpend Sokoli, have been…
New Linux Rootkit PUMAKIT Uses Advanced Stealth Techniques to Evade Detection
[ad_1] Dec 13, 2024Ravie LakshmananLinux / Threat Analysis Cybersecurity researchers have uncovered a new Linux rootkit called PUMAKIT that comes with capabilities to escalate privileges, hide files and directories, and conceal itself from system tools, while simultaneously evading detection. “PUMAKIT is a sophisticated loadable kernel module (LKM) rootkit that employs advanced stealth mechanisms to hide…
How to Generate a CrowdStrike RFM Report With AI in Tines
[ad_1] Run by the team at orchestration, AI, and automation platform Tines, the Tines library contains pre-built workflows shared by real security practitioners from across the community, all of which are free to import and deploy via the Community Edition of the platform. Their bi-annual “You Did What with Tines?!” competition highlights some of the…
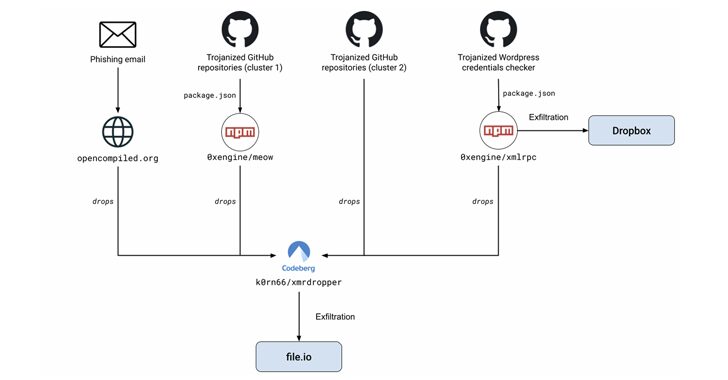
390,000+ WordPress Credentials Stolen via Malicious GitHub Repository Hosting PoC Exploits
[ad_1] Dec 13, 2024Ravie LakshmananCyber Attack / Malware A now-removed GitHub repository that advertised a WordPress tool to publish posts to the online content management system (CMS) is estimated to have enabled the exfiltration of over 390,000 credentials. The malicious activity is part of a broader attack campaign undertaken by a threat actor, dubbed MUT-1244…
Iran-Linked IOCONTROL Malware Targets SCADA and Linux-Based IoT Platforms
[ad_1] Dec 13, 2024The Hacker NewsIoT Security / Operational Technology Iran-affiliated threat actors have been linked to a new custom malware that’s geared toward IoT and operational technology (OT) environments in Israel and the United States. The malware has been codenamed IOCONTROL by OT cybersecurity company Claroty, highlighting its ability to attack IoT and supervisory…