[ad_1] The U.S. Department of Justice (DoJ) has indicted 14 nationals belonging to the Democratic People’s Republic of Korea (DPRK or North Korea) for their alleged involvement in a long-running conspiracy to violate sanctions and commit wire fraud, money laundering, and identity theft by illegally seeking employment in U.S. companies and non-profit organizations. “The conspirators,…
Month: December 2024
Critical OpenWrt Vulnerability Exposes Devices to Malicious Firmware Injection
[ad_1] Dec 13, 2024The Hacker NewsLinux / Vulnerability A security flaw has been disclosed in OpenWrt‘s Attended Sysupgrade (ASU) feature that, if successfully exploited, could have been abused to distribute malicious firmware packages. The vulnerability, tracked as CVE-2024-54143, carries a CVSS score of 9.3 out of a maximum of 10, indicating critical severity. Flatt Security…
Gamaredon Deploys Android Spyware “BoneSpy” and “PlainGnome” in Former Soviet States
[ad_1] Dec 12, 2024Ravie LakshmananMobile Security / Cyber Espionage The Russia-linked state-sponsored threat actor tracked as Gamaredon has been attributed to two new Android spyware tools called BoneSpy and PlainGnome, marking the first time the adversary has been discovered using mobile-only malware families in its attack campaigns. “BoneSpy and PlainGnome target former Soviet states and…
Credentials and API Keys Leaking Online
[ad_1] Dec 12, 2024Ravie LakshmananVulnerability / Cloud Security Cybersecurity researchers are warning that thousands of servers hosting the Prometheus monitoring and alerting toolkit are at risk of information leakage and exposure to denial-of-service (DoS) as well as remote code execution (RCE) attacks. “Prometheus servers or exporters, often lacking proper authentication, allowed attackers to easily gather…
Europol Dismantles 27 DDoS Attack Platforms Across 15 Nations; Admins Arrested
[ad_1] Dec 12, 2024Ravie LakshmananCyber Crime / DDoS Attack A global law enforcement operation has failed 27 stresser services that were used to conduct distributed denial-of-service (DDoS) attacks and took them offline as part of a multi-year international exercise called PowerOFF. The effort, coordinated by Europol and involving 15 countries, dismantled several booter and stresser…
Secret Blizzard Deploys Kazuar Backdoor in Ukraine Using Amadey Malware-as-a-Service
[ad_1] Dec 11, 2024Ravie LakshmananMalware / Cyber Espionage The Russian nation-state actor tracked as Secret Blizzard has been observed leveraging malware associated with other threat actors to deploy a known backdoor called Kazuar on target devices located in Ukraine. The new findings come from the Microsoft threat intelligence team, which said it observed the adversary…
New Malware Technique Could Exploit Windows UI Framework to Evade EDR Tools
[ad_1] Dec 11, 2024Ravie LakshmananMalware / Endpoint Security A newly devised technique leverages a Windows accessibility framework called UI Automation (UIA) to perform a wide range of malicious activities without tipping off endpoint detection and response (EDR) solutions. “To exploit this technique, a user must be convinced to run a program that uses UI Automation,”…
Microsoft Fixes 72 Flaws, Including Patch for Actively Exploited CLFS Vulnerability
[ad_1] Microsoft closed out its Patch Tuesday updates for 2024 with fixes for a total of 72 security flaws spanning its software portfolio, including one that it said has been exploited in the wild. Of the 72 flaws, 17 are rated Critical, 54 are rated Important, and one is rated Moderate in severity. Thirty-one of…
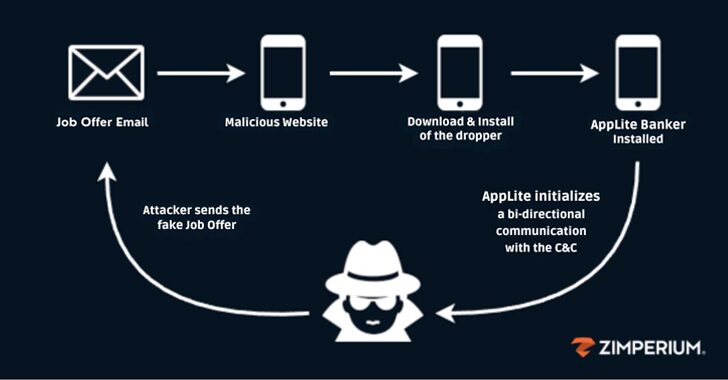
Fake Recruiters Distribute Banking Trojan via Malicious Apps in Phishing Scam
[ad_1] Dec 10, 2024Ravie LakshmananMobile Security / Cryptocurrency Cybersecurity researchers have shed light on a sophisticated mobile phishing (aka mishing) campaign that’s designed to distribute an updated version of the Antidot banking trojan. “The attackers presented themselves as recruiters, luring unsuspecting victims with job offers,” Zimperium zLabs Vishnu Pratapagiri researcher said in a new report….
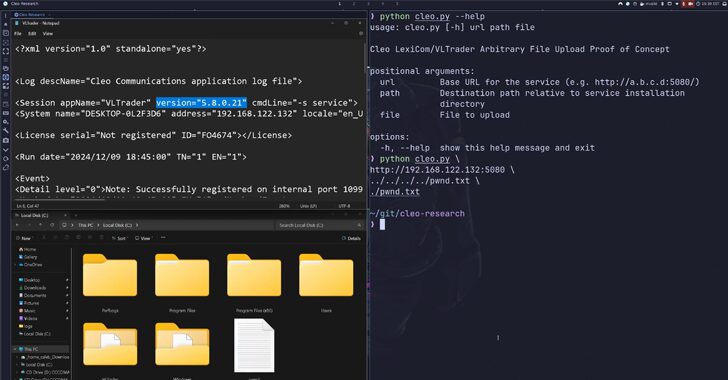
Cleo File Transfer Vulnerability Under Exploitation – Patch Pending, Mitigation Urged
[ad_1] Dec 10, 2024Ravie LakshmananVulnerability / Threat Analysis Users of Cleo-managed file transfer software are being urged to ensure that their instances are not exposed to the internet following reports of mass exploitation of a vulnerability affecting fully patched systems. Cybersecurity company Huntress said it discovered evidence of threat actors exploiting the issue en masse…