[ad_1] May 17, 2024NewsroomVulnerability / Network Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added two security flaws impacting D-Link routers to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The list of vulnerabilities is as follows – CVE-2014-100005 – A cross-site request forgery (CSRF) vulnerability impacting D-Link…
Category: Cyber News
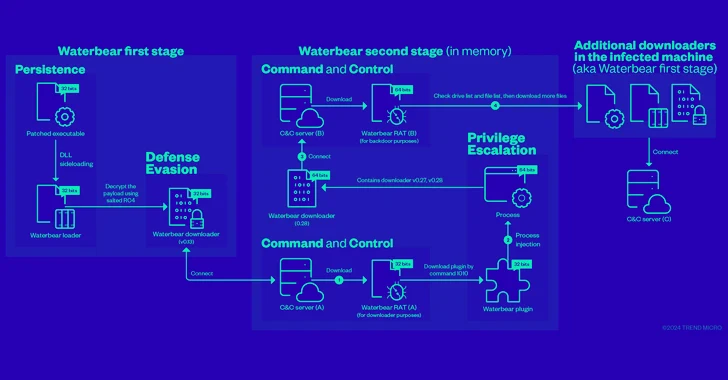
China-Linked Hackers Adopt Two-Stage Infection Tactic to Deploy Deuterbear RAT
[ad_1] Cybersecurity researchers have shed more light on a remote access trojan (RAT) known as Deuterbear used by the China-linked BlackTech hacking group as part of a cyber espionage campaign targeting the Asia-Pacific region this year. “Deuterbear, while similar to Waterbear in many ways, shows advancements in capabilities such as including support for shellcode plugins,…
80% of Exposures from Misconfigurations, Less Than 1% from CVEs
[ad_1] A new report from XM Cyber has found – among other insights – a dramatic gap between where most organizations focus their security efforts, and where the most serious threats actually reside. The new report, Navigating the Paths of Risk: The State of Exposure Management in 2024, is based on hundreds of thousands of…
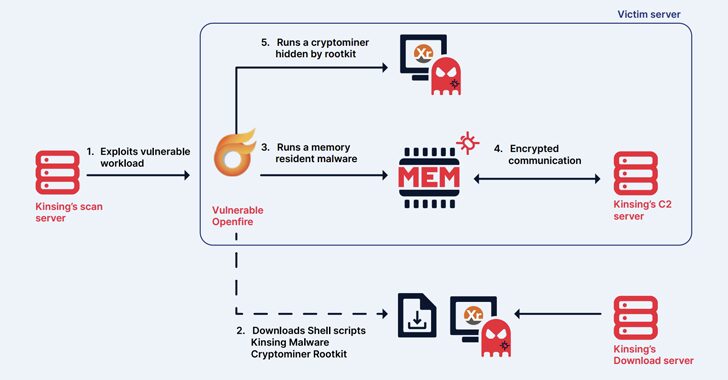
Kinsing Hacker Group Exploits More Flaws to Expand Botnet for Cryptojacking
[ad_1] May 17, 2024NewsroomCryptojacking / Malware The cryptojacking group known as Kinsing has demonstrated its ability to continuously evolve and adapt, proving to be a persistent threat by swiftly integrating newly disclosed vulnerabilities to exploit arsenal and expand its botnet. The findings come from cloud security firm Aqua, which described the threat actor as actively…
Kimsuky APT Deploying Linux Backdoor Gomir in South Korean Cyber Attacks
[ad_1] May 17, 2024NewsroomLinux / Malware The Kimsuky (aka Springtail) advanced persistent threat (APT) group, which is linked to North Korea’s Reconnaissance General Bureau (RGB), has been observed deploying a Linux version of its GoBear backdoor as part of a campaign targeting South Korean organizations. The backdoor, codenamed Gomir, is “structurally almost identical to GoBear,…
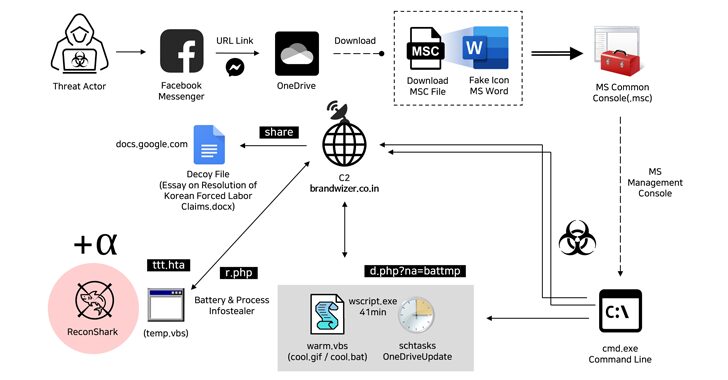
North Korean Hackers Exploit Facebook Messenger in Targeted Malware Campaign
[ad_1] May 16, 2024NewsroomMalware / Cyber Espionage The North Korea-linked Kimsuky hacking group has been attributed to a new social engineering attack that employs fictitious Facebook accounts to targets via Messenger and ultimately delivers malware. “The threat actor created a Facebook account with a fake identity disguised as a public official working in the North…
New Wi-Fi Vulnerability Enables Network Eavesdropping via Downgrade Attacks
[ad_1] May 16, 2024NewsroomVulnerability / Network Security Researchers have discovered a new security vulnerability stemming from a design flaw in the IEEE 802.11 Wi-Fi standard that tricks victims into connecting to a less secure wireless network and eavesdrop on their network traffic. The SSID Confusion attack, tracked as CVE-2023-52424, impacts all operating systems and Wi-Fi…
Researchers Uncover 11 Security Flaws in GE HealthCare Ultrasound Machines
[ad_1] Security researchers have disclosed almost a dozen security flaws impacting the GE HealthCare Vivid Ultrasound product family that could be exploited by malicious actors to tamper with patient data and even install ransomware under certain circumstances. “The impacts enabled by these flaws are manifold: from the implant of ransomware on the ultrasound machine to…
FBI Seizes BreachForums Again, Urges Users to Report Criminal Activity
[ad_1] May 15, 2024NewsroomData Breach / Cyber Crime Law enforcement agencies have officially seized control of the notorious BreachForums platform, an online bazaar known for peddling stolen data, for the second time within a year. The website (“breachforums[.]st”) has been replaced by a seizure banner stating the clearnet cybercrime forum is under the control of…
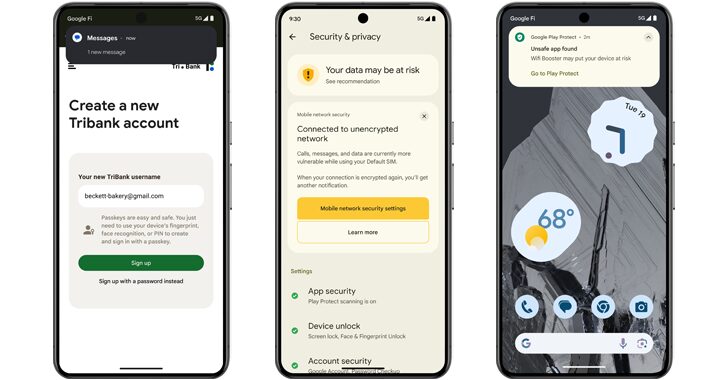
Android 15 Rolls Out Advanced Features to Protect Users from Scams and Malicious Apps
[ad_1] May 15, 2024NewsroomAndroid Security / Malware Google is unveiling a set of new features in Android 15 to prevent malicious apps installed on the device from capturing sensitive data. This constitutes an update to the Play Integrity API that third-party app developers can take advantage of to secure their applications against malware. “Developers can…